Now that I’ve completed the hardware setup from my last post (if you missed the hardware, SPI flash, power issues etc, please check it out) the next step is to get this system up and running as my new desktop. So far during the build performance has been excellent and I’m looking forward to the Rock 5B software running. Here are my functional requirements:
- Chrome or equivalent (Chromium) with the ability to sync bookmarks, history and the ability to “send” a page from my phone to the Rock 5B browser
- VSCode for development either on the Rock 5B directly, or using remote SSH from the Rock 5B to other devices (i.e. Raspberry Pi’s, VM’s, etc)
- Cura for creating my 3D print gcode files
- Blender for editing and exporting STL files for Cura
- Libre Office for some basic office compatibility (where web versions are not ideal)
- Docker for deploying and testing applications like WordPress, ModSecurity, NGiNX, FreeRadius, MySQL, etc
- AD integration for authentication
- Duo for 2-Factor authentication
- RDP and SSH access from my Chromebook or Windows laptops
So lets get started with some basics.
| Part | Link | Cost (at time of writing) |
|---|---|---|
| Radxa Rock 5B (8GB) | At Ameridroid | $169.95 |
| Crucial P3 500GB PCIe Gen3 NVMe SSD (optional) | At Amazon | $34.99 |
| M.2 SSD Heatsink (optional) | At Amazon | $10.99 |
| 64GB eMMC (optional) | At AliExpress | $39.98 |
| Heatsink | At Amazon | $11.99 |
| Total (with options) | $267.90 |
System Basic Packages
First off Ubuntu server image available from Radxa GitHub repo (https://github.com/radxa-build/rock-5b/releases/tag/20221101-0103) has no GUI and since I am running this as a desktop system I need to get the Ubuntu desktop installed.
sudo apt update
Whoops. First issue. The public key for the Radxa apt server is expired. Odd, but Radxa has a fix for it called out in their FAQ (https://wiki.radxa.com/Rock5/FAQs):
sudo apt install wget
wget -O – apt.radxa.com/focal-stable/public.keyNOTE: The FAQ uses ‘bullseye-stable’ for Debian. Switching to ‘focal-stable’ works fine for Ubuntu 20.04.
Now that the public key is installed, the certificate errors are gone so we can move on to installing the desktop.
sudo apt update && sudo apt upgrade
sudo apt install ubuntu-desktop
sudo systemctl set-default graphical.target
sudo reboot
After installing the GUI and rebooting we are now at the normal Ubuntu login! Next for the Rock 5B software setup is installing some basic tools that I install on all my systems. All of these tasks are run via Ansible. What is listed from this point on is a summary of the tasks run by the Ansible script:
sudo apt update && sudo apt install tmux vim curl wget nano python3 python3-pip python3-wheel python3-cryptography expect libfs-util nfs-common git cifs-utils rsyslogInstalling the packages needed for AD authentication:
sudo apt update && sudo apt install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients policycoreutils-python-utilsXRDP for using the RDP client to connect from my windows laptop:
sudo apt update && sudo apt install xrdpDocker has a documented process for installing on Ubuntu located here: https://docs.docker.com/engine/install/ubuntu/. Boiling it down to the required, first remove any old versions or versions that are packaged with your distro:
sudo apt remove docker docker-engine docker.io containerd runcNOTE: These packages may not be present. If they aren’t, no worries, just move on and install the pre-requisite packages.
sudo apt update && sudo apt install ca-certificates curl gnupg lsb-releaseNext is installing the Docker GPG key (prevents the apt errors we saw with Radxa earlier) and create the repo file.
sudo mkdir -p /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg
echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
Last is installing the docker packages.
sudo apt update && sudo apt install docker-ce docker-ce-cli containerd.io docker-compose-pluginIf you would like to test, you can run docker’s hello-world image that will give you a “Hello from Docker!” message to let you know things are working.
sudo docker run hello-worldNow that docker is running, I have some basic config that I apply to allow for remote API access and to set logging levels. This will require editing the contents of the /etc/docker/daemon.json file (create it if it doesn’t exist). Here is the content of my standard file:
{
"log-driver": "json-file",
"log-opts": {
"max-size": "10m",
"max-file": "5"
},
"tlsverify": true,
"tlscacert": “...”,
"tlscert": “...”,
"tlskey": "...",
"hosts": [
"unix:///var/run/docker.sock",
"tcp://0.0.0.0:2376"
],
"containerd": "/run/containerd/containerd.sock"
}
The config here is to set logging to use a JSON file (which is technically the default, but I prefer to explicitly define it since I am also defining some options) with a max size and maximum number of files. Info on logging drivers and options can be found here: https://docs.docker.com/config/containers/logging/configure/
NOTE: Changing the default logging driver or drover options only affects containers that are created after the change. Existing containers will retain their logging driver settings. This is why I always set this when docker is installed.
The TLS settings are to enable client key verification and provide the path to the CA cert, server cert and key files. I use this to manage docker from a central host. The “hosts” section enabled the API via the docker.sock socket, or on TCP port 2376.
You can simply remove the “tls…” and “hosts” entries if you don’t intend to use the API.
Now that my Rock 5B software has all the main system tools I need, I’ll move on to client applications.
Installing the Client Applications
LibreOffice, Blender and Cura (for creating/editing STL files, and for slicing the STL files into GCODE for my 3D printer) are available in the default Ubuntu APT repository. The downside is that these packages for Blender and Cura are a bit out of date. APT has Blender 2.82 and Cura 4.4.1. Blender is currently at 3.4.1 and Cura is at 5.2.1. I attempted to download and compile Cura from source, but this turned out to be a bust in the end. After hours of hashing through requirements and attempting to get the compile running I ended up with a CMake version error. Ubuntu 20.04 has 3.16.3 and 3.20 or higher is required. I ended up ditching the compile from source and running the versions available in APT.
sudo apt update && sudo apt install libreoffice cura blenderVSCode install is well documented on visualstudio.com: https://code.visualstudio.com/docs/setup/linux. Microsoft has a repository that can be added to the system to install and update VSCode. The relevant instructions are:
sudo apt update && sudo apt install wget gpg apt-transport-https
wget -qO- https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor > packages.microsoft.gpg
sudo install -D -o root -g root -m 644 packages.microsoft.gpg /etc/apt/keyrings/packages.microsoft.gpg
sudo sh -c 'echo "deb [arch=amd64,arm64,armhf signed-by=/etc/apt/keyrings/packages.microsoft.gpg] https://packages.microsoft.com/repos/code stable main" > /etc/apt/sources.list.d/vscode.list'
rm -f packages.microsoft.gpg
sudo apt update && sudo apt install code
The last major application is Chrome. The issue here is Google has yet to release a Linux ARM version of Chrome so we are limited to Chromium. Google ALSO has decided to disable synchronization with Chromium which limits the functionality of Chromium and eliminates the whole reason I use Chrome. I run Chrome on my desktop, Phone, Chromebook, and Windows laptop. The ability to share bookmarks, history and also to send a page from one device to another is something that I have become accustomed to and not willing to live without.
After LOTS of time searching the internet and reading posts that claim to have the fix for syncing with Chromium I finally found a working solution! Given the length that it takes to put together I created a whole separate post for configuring Chromium with Chrome here: https://www.learningtopi.com/sbc/chromium-sync/
The end result is yes, you CAN sync Chromium with Chrome as long as you can get through all the steps required. So far I have been running with no issues and have been able to send pages from my phone to my Rock 5B. On occasion if I don’t get the sent page notification closing and reopening Chromium gets the popup.
At this point the Rock 5B software setup is complete. I have all the major tools and applications I run on a daily basis ready to go. From here I ran into some performance issues that we can dig into:
Memory Issues
I purchased the 8GB version of the Rock 5B, but I still ran into slowness and lock up issues when I saw the memory utilization get high. After a quick check of “free -h”, I found a complete lack of swap space. I’ve run across this before on images provided for SBC systems. If the device utilizes an SD card for primary storage, you certainly do not want to use a swap partition or file. I also know from experience that not having ANY swap space will eventually come back to bite you when running a graphical system. Chromium alone will take up gigs of RAM if you open tabs like I do!
I started out by trying to configure zram. This is a package that uses essentially a ramdisk to hold compressed pages that are swapped out of main RAM. The advantage here is that if you are starting to run low on memory, the system can page out less frequently used data to the zram “disk” which is just a compressed space in RAM. I have found that enabling this feature prevents crashing and system locks when memory usage gets high.
After attempting to configure zram, I found that the developers had included the zram module into the kernel! You can verify in your Rock 5B (or any other SBC) by using:
### For modules built into the kernel
awk -F"/" '{print $NF}' /lib/modules/`uname -r`/modules.builtin | cut -d "." -f1
### For modules that are compiled as .ko files and can be inserted into the kernel
find /sys/module/ -type f -name "initstate" -print | awk -F"/" '{print $(NF-1)}'
If ‘zram’ is listed (as it is in the case of the Rock5B Ubuntu kernel) then you may run into a problem when running the zram service. The crux of the issue is that zram expects a ‘zram device’ for each logical CPU, however the kernel is only creating a single. This can be corrected by passing the proper number of devices to the kernel module on bootup. For the Rock 5B, this can be done by editing the ‘/boot/config.txt’ file to include:
cmdline: zram.num_devices=8After ANY edits to the ‘/boot/config.txt’ file you MUST run ‘sudo update_extlinux.sh’ to update the ‘/boot/extlinux/extlinux.conf’ file. This script will update the kernel boot to include any configuration placed in the ‘/boot/config.txt’ file.
After the edit, reboot, then you can check that your zram devices are present with ‘zramctl’ and that your swap is available with ‘free -h’.
XRDP
Many die-hard UNIX users will probably balk at this, but I prefer to use remote desktop to access remote systems. I’ve found this to be universally supported on different platforms (Windows, Linux, Android, etc) and typically faster and easier to use than VNC. RDP also allows you to select the resolution based on the client connecting rather than based on the host (like VNC) so you lose a lot of scaling artifacts.
Installing is easy with the apt package:
sudo apt update && sudo apt install xrdpAfter installing, the service can be configured using the ‘/etc/xrdp/xrdp.ini’ file. Since I am using this only to RDP into this system, I’ve commented out the ‘[Xvnc]’, ‘[vnc-any]’, ‘[neutrinordp-any]’ sections and left only the ‘[Xorg]’. No other changes are required. If you leave the other sections, the XRDP service may be used to jump to other systems which may not be desirable.
After logging in with a remote desktop client, you will get an ‘Authentication Required’ prompt to create a ‘color managed device’. This can be fixed by updating the polkit to allow the action.
First make sure you are running as root (using ‘sudo su’) and create the following file: /etc/polkit-1/localauthority/50-local.d/45-allow-colord.pkla
Source: http://c-nergy.be/blog/?p=13641
Allow Colord all Users]
Identity=unix-user:*
Action=org.freedesktop.color-manager.create-device;org.freedesktop.color-manager.create-profile;org.freedesktop.color-manager.delete-device;org.freedesktop.color-manager.delete-profile;org.freedesktop.color-manager.modify-device;org.freedesktop.color-manager.modify-profile
ResultAny=no
ResultInactive=no
ResultActive=yesYou can also fix the missing task bar by updating the xrdp startwm.sh file (source: https://superuser.com/questions/1479313/how-do-i-get-the-full-ubuntu-gnome-experience-via-xrdp) using the following 3 commands:
sudo sed -i '4 i\export XDG_CURRENT_DESKTOP=ubuntu:GNOME' /etc/xrdp/startwm.sh
sudo sed -i '4 i\export GNOME_SHELL_SESSION_MODE=ubuntu' /etc/xrdp/startwm.sh
sudo sed -i '4 i\export DESKTOP_SESSION=ubuntu' /etc/xrdp/startwm.sh
UPDATE – 4/1/2023
In addition to the ‘Authentication Required’ for the ‘color managed device’, I found that I was receiving frequent pop ups with the following:
Authentication required to refresh system repositories
After finally being irritated enought to search for a solution, I found a similar polkit fix here: https://c-nergy.be/blog/?p=14051
Adding the following contents to the file /etc/polkit-1/localauthority/50-local.d/46-allow-update-repo.pkla resolved this once and for all!
[Allow Package Management all Users]
Identity=unix-user:*
Action=org.freedesktop.packagekit.system-sources-refresh
ResultAny=yes
ResultInactive=yes
ResultActive=yesWindows Active Directory Authentication
Hard-core UNIX users may ALSO balk at this, however I do run Windows AD for centralized authentication for systems and applications as well as for local certificate services. This will use the sssd service for authentication. The packages and prerequisites can be installed using APT:
sudo apt update && sudo apt upgrade sssd sssd-tools realmd oddjob oddjob-mkhomedir adcli samba-common sssd-krb5 policycoreutils-python-utils krb5-userOnce the packages are installed, you can check to verify that the realm is available using:
realm discover [domain-name]After you verify that the realm can be found, join it:
realm join -U [admin-user] [domain-name]After the join is complete, the basic configuration will be added to the ‘/etc/sssd/sssd.conf’ file. I update this to modify a few default settings and to set the ldap id map ranges so the user ID’s will be consistent across all systems. Here are the contents of my sssd.conf file:
[sssd]
domains = [domain-name]
config_file_version = 2
services = nss, pam
[domain/[domain-name]]
ad_domain = [domain-name]
krb5_realm = [domain-name]
realmd_tags = manages-system joined-with-adcli
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = False
override_homedir = /home/%d/%u
access_provider = simple
ldap_idmap_autorid_compat = True
ldap_idmap_range_min = 10000001
ldap_idmap_range_max = 20000000
ldap_idmap_range_size = 9999999
enumerate = True
dyndns_update = False
After updating things like the idmap range, you need to stop and clear the sssd cache before things will function properly. That can be done using the following:
sudo systemctl stop sssd
sudo rm /var/lib/sss/db/*
sudo systemctl start sssd
User home directories will be placed in the /home/[domain-name]/[user-name] folders. I have on occasion found that the folders are not created properly using oddjob, so they directories can be created manually:
sudo mkdir -p /home/[domain-name]/[username]
sudo chown [username]:[group] -r /home/[domain-name]/[username]
If this was a system with lots of users I would probably look for a more long term fix, but this works for me.
Once finished you should be able to log into the Ubuntu login on the console as well as via SSH using your AD credentials.
DUO 2 Factor Authentication
I use DUO for SSH and XRDP login access on all my systems. 2FA has become a standard in most enterprises, and I felt like there was no reason not to do the same. DUO has a free version with a limited number of users which works perfectly for my needs so there is no cost.
Sadly, DUO also does not have a Linux ARM build available, so you need to install from source
sudo apt update && sudo apt install libssl-dev libpam-dev gccDownload DUO from the site (and verify the SHA-256 checksum) (downloads available on DUO https://duo.com/docs/checksums#duo-unix):
wget https://dl.duosecurity.com/duo_unix-2.0.0.tar.gz
sha256sum duo_unix-2.0.0.tar.gz
After verifying the checksum, extract, compile and install:
tar xfvz duo_unix-2.0.0.tar.gz && cd duo_unix-2.0.0 && ./configure --with-pam --prefix=/usr && make && sudo make installOnce the install is complete, DUO can be configured using the “/etc/duo/pam_duo.conf” file. The following us the general config that I use for push notifications:
[duo]
; Duo integration key
ikey = ...
; Duo secret key
skey = ...
; Duo API host
host = ...
; `failmode = safe` In the event of errors with this configuration file or connection to the Duo service
; this mode will allow login without 2FA.
; `failmode = secure` This mode will deny access in the above cases. Misconfigurations with this setting
; enabled may result in you being locked out of your system.
failmode = safe
; Send command for Duo Push authentication
;pushinfo = yes
groups = *admins, sudo, wheel
autopush = yes
prompts = 1
The groups are the groups of users that you want to force DUO 2FA for. “sudo” and “wheel” are the sudoers groups for Ubuntu and Red Hat so I always include these. Since I am also going to include AD Authentication, I include a “*admins” wildcard to include the Domain Admins, Enterprise Admins, etc groups.
The ikey, skey and host should be copied from your protected application in the DUO Admin console. If you are new to DUO, after creating your free account select Applications, then Protect an Application.
NOTE: Additional configuration options can be found on the duounix docs page: https://duo.com/docs/duounix
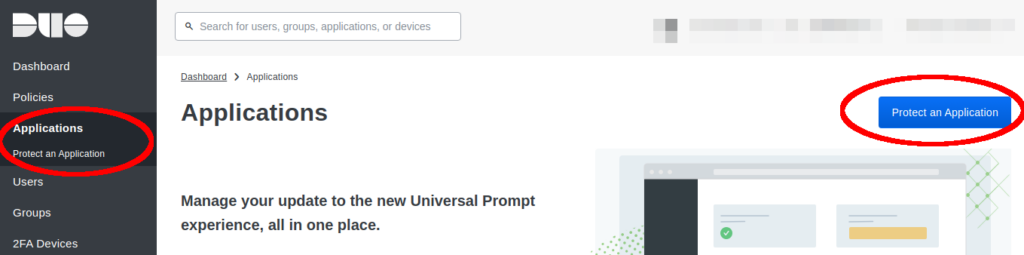
From the list, search for “unixapp” and select protect. This will take you to a new page that will list the ikey, skey, and host for your application.
Copy your keys. You can re-use the same set of keys on multiple systems, or you can create a new unix application if you prefer to protect systems individually.
Once DUO is configured, the next step is to configure PAM (the Linux Pluggable Authentication Module). In the /etc/pam.d folder you’ll find files for different applications as well as general system files. I’m going to enable DUO 2FA for all SSH and XRDP logins only (excluding when I’m logging into to the system locally). To do this, I’m going to edit the “sshd” and “xrdp-sesman” files in the “/etc/pam.d” folder.
First, make sure you have the path to the ‘pam_duo.so’ file. When compiling from source and installing it is located in ‘/usr/lib/security/pam_duo.so’. If you found this page and are using DUO from an APT package, you can check the path using ‘dpkg -L duo-unix | grep -I pam_duo.so’ for Debian/Ubuntu based systems. For RedHat RPM based systems you can use ‘rpm -ql duo_unix pam_duo | grep -I pam_duo.so’.
Edit the /etc/pam.d/sshd file (using sudo vim or sudo nano or whatever you preferred editor is) and add the following AFTER the “@include common-auth” line:
@include common-auth
auth [success=1 default=ignore] /usr/lib/security/pam_duo.so ## Replace with proper path!
auth requisite pam_deny.so
auth required pam_permit.so
Also in the ‘/etc/ssh/sshd_config‘ file, search for and make sure that the following are set:
UsePAM yes
ChallengeResponseAuthentication yes
UseDNS no
If you had to make any changes in the sshd_config file, be sure to restart the ssh service!
NOTE: Disabling DNS allows the IP of the device to be sent to the push notification rather than a reverse-DNS lookup. This is DUO’s recommendation.
If you are using public key authentication and have “PasswordAuthentication no” set, you MUST add “AuthenticationMethods publickey,keyboard-interactive” otherwise the push will fail!
Once this is set, DUO push notification to your mobile device works when you log in via SSH. If you are running XRDP, you can make the same changes in the ‘/etc/pam.d/xrdp-sesman’ file.
Wrap Up
Now that everything is installed and have been using the Rock 5B for some time and I am impressed! Performance wise I have no complaints. The system (running on the eMMC) is quick and responsive, and all applications are working properly! I have noticed no issues running Blender, Cura, VSCode or Chromium. The system performance has been impressive enough to meet my high hopes for a GPIO capable ARM desktop.
I can actually say that connecting via XRDP is quicker and more responsive than connecting to a similar Ubuntu VM running on my home server!
If you are looking for a low cost ARM desktop system, the Rock 5B is worth a look. My Raspberry Pi 4B was always decent, but even running on a USB3 connected SSD performance for graphical applications (Chromium in particular) was a bit dismal.
Up Next
Now that the system is up and operational, the next step is building a test suite to compare real world maker functionality between platforms. This will include some basics light LED’s and buttons as well as more complex systems like I2C displays, SPI sensors, DHT11/22 and serial I/O.
Stay tuned to our Rock 5B channel!

Hi,
Thank you for this its a very great help and followed your instructions.
Can I please ask for help because I have followed your instructions and I got the desktop working but I have the OS installed on my SDcard. Is there a way to transfer this to SSD?
Also, one other program that I need to use is Zoom. How do you go about installing this based on your setup? I tried installing flatpak but it doesn’t work.
For a regular desktop user, all you really need is firefox, libreoffice and zoom I think. Zoom is just the one that is missing.
Thank you.
Hans
Moving your install image from one media to another should be as simple as running dd to copy the contents of the SD to SSD. I haven’t tested this specifically on the Rock 5B, but will give it a shot in the future. From some searching it looks like Zoom doesn’t have an ARM64 client install (https://devforum.zoom.us/t/zoom-client-for-arm-based-systems/21980/19). Given that the Rock 5B has a more powerfull CPU and (depending on your system) more RAM, you may be able to get by with the web based version. The biggest downside to ARM based computers is a lack of software support.
Hi ,
A big thank you for the tutorial
I followed your instructions and everything works except mouse pointer disappears but mouse action still works.
To get mouse pointer back I have to power-off and restart.
Mouse pointer disappears when:
1 – on blank screen – power saving (no set to never)
2 – if no screen activity (have to check this further)
Have I msised something?
/Gerry
I haven’t seen an issue with the mouse pointer previously. Is this connecting via RDP to a Rock 5B running XRDP, or is this locally on the console?